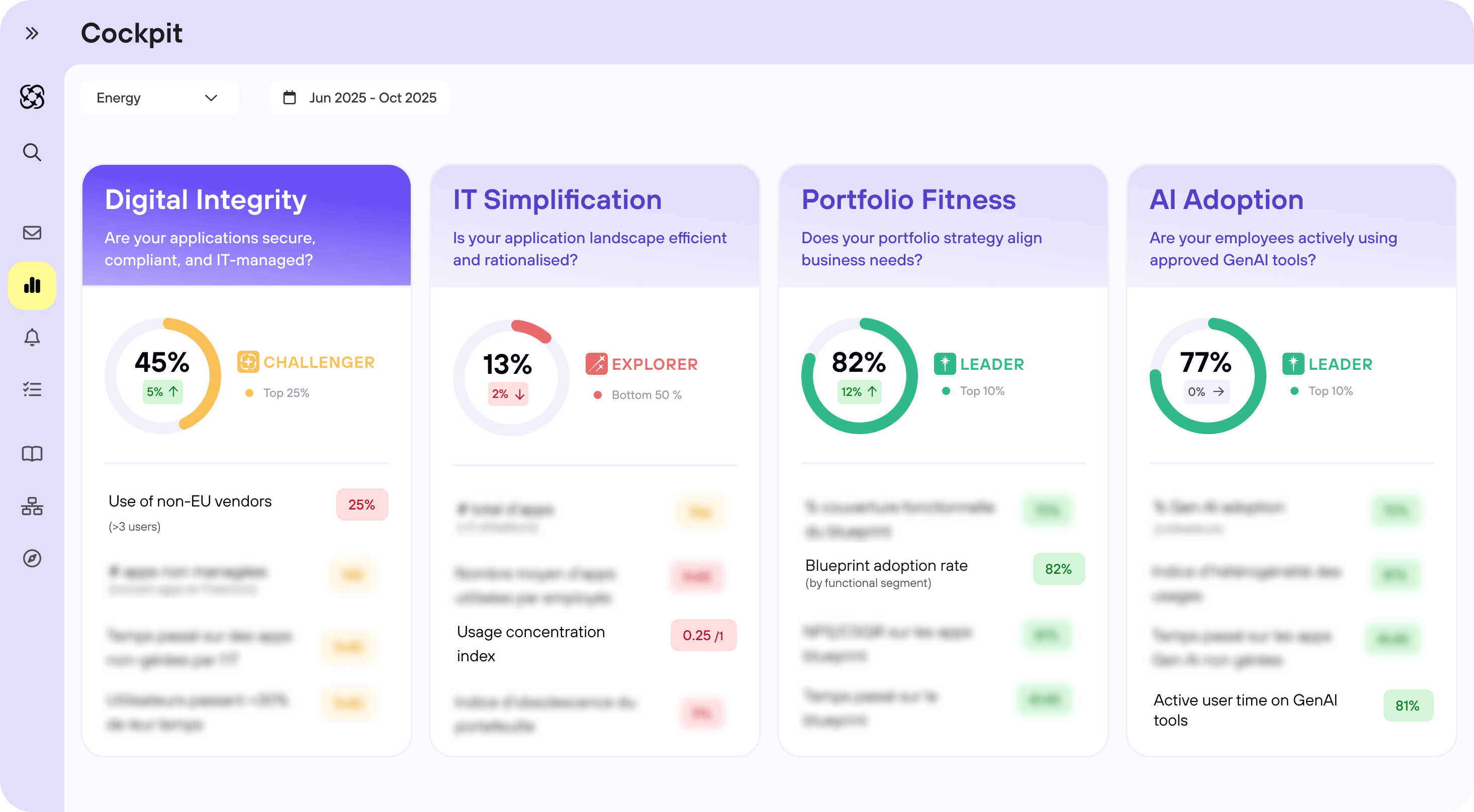
Digital Integrity
Strengthen your security strategies
Gain full visibility into risky application usage and automatically redirect employees towards secure, IT-managed alternatives.
WITH TRADITIONAL TOOLS
- Limited visibility over shadow IT usage
- Blocking decisions based solely on risk
- Blocked applications that disrupt business operations.
POWERED BY BEAMY
- Automated mapping of all applications in use
- Large-scale qualification of business criticality
- Contextualised blocking with seamless redirection to secure alternatives
1452
Unlisted apps detected (≥ 5 users)
+112
Apps blocked after assessment of business criticality
-15%
Time spent on shadow IT apps thanks to automated redirection
Identify and map all applications used
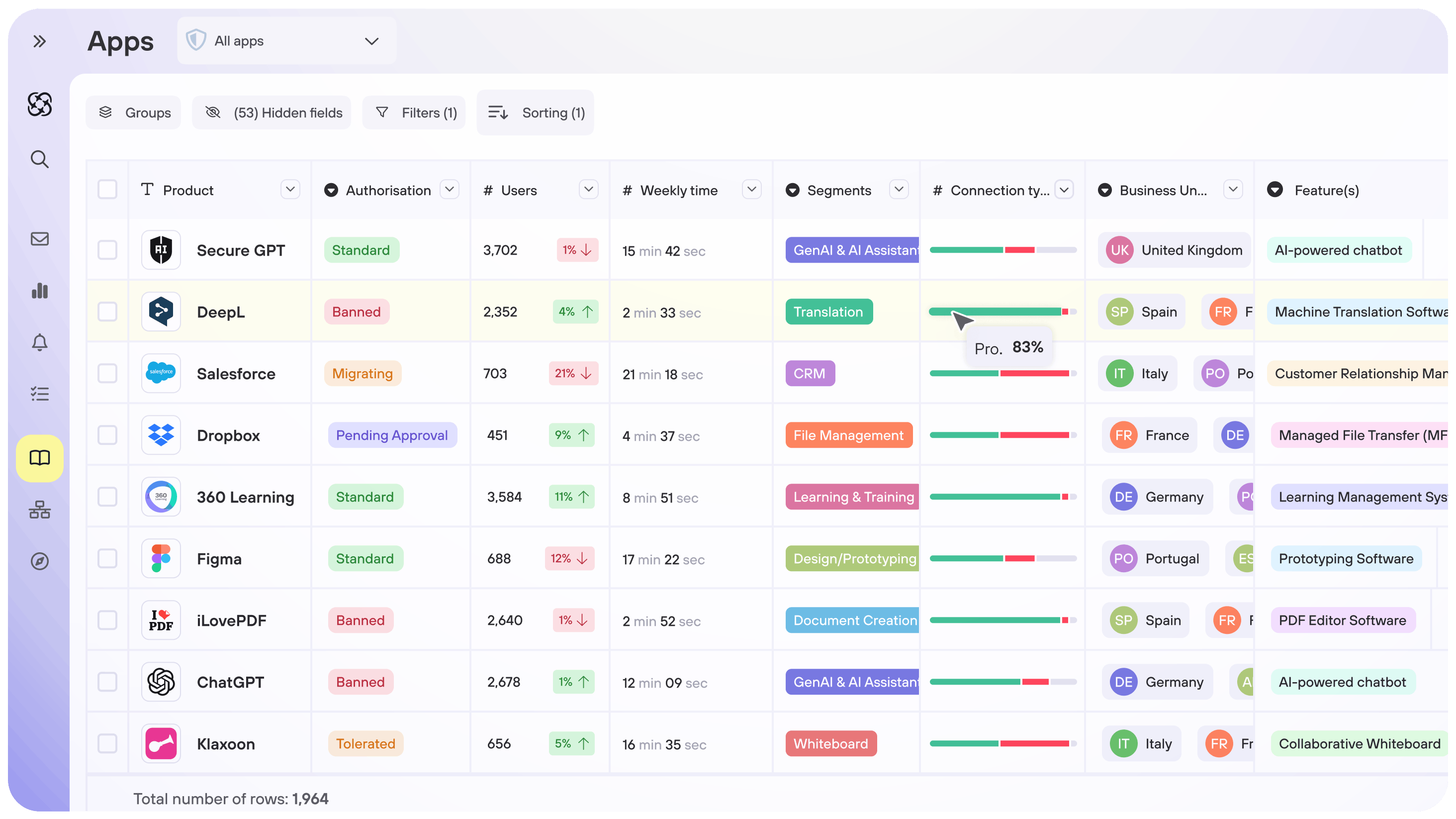
- Automatically detect and reference 100% of applications (public SaaS and internal tools)
- Measure application usage to determine business criticality
- Synchronise and enrich your IT repositories (SSE, CMDB, APM)
Assess the business criticality of risky applications
- Launch investigation surveys within minutes using ready-to-use templates
- Collect feedback from business teams to assess each application’s criticality
- Consolidate insights to prioritise blocking or validation decisions
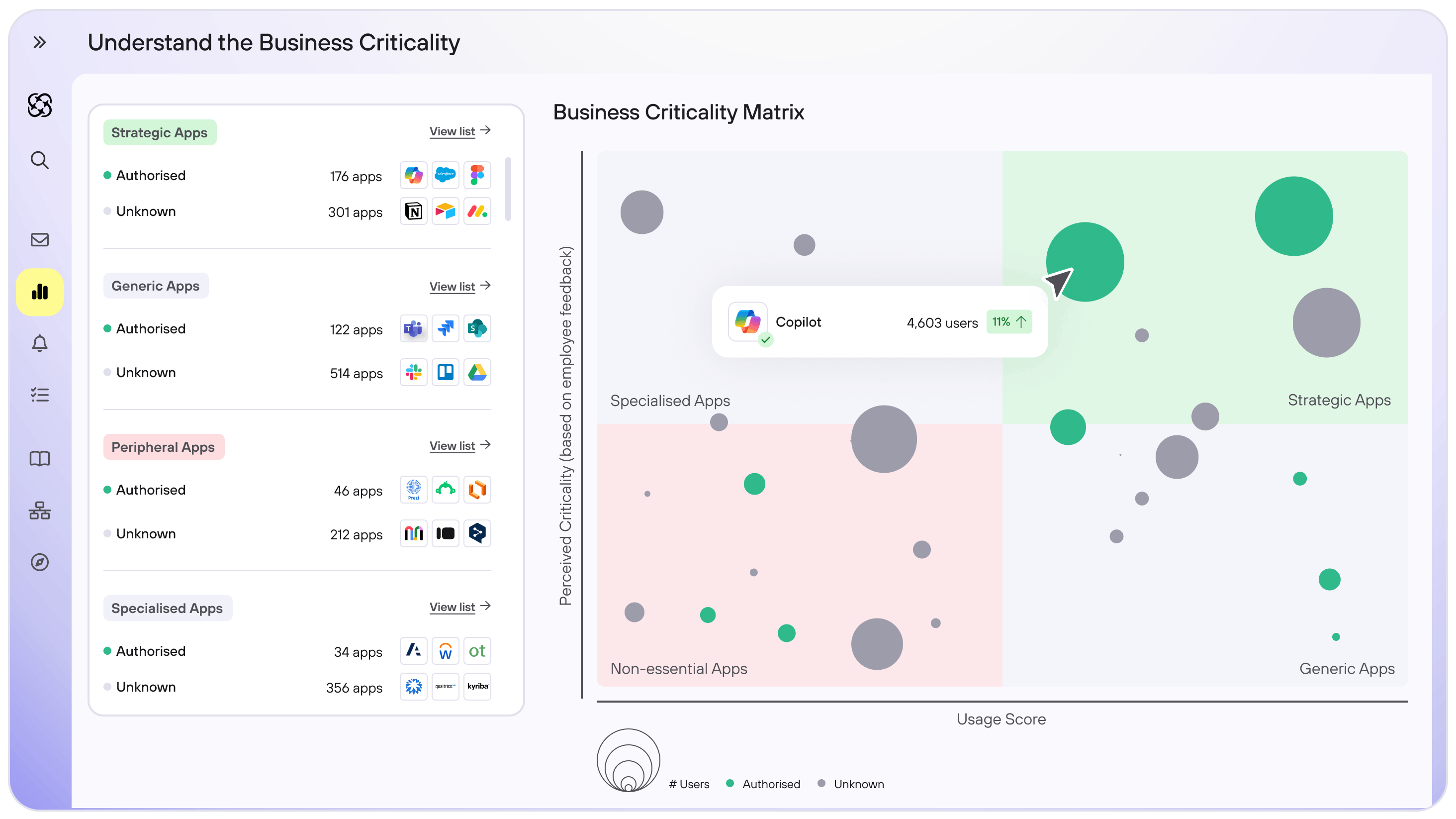
Optimise your blocking strategy
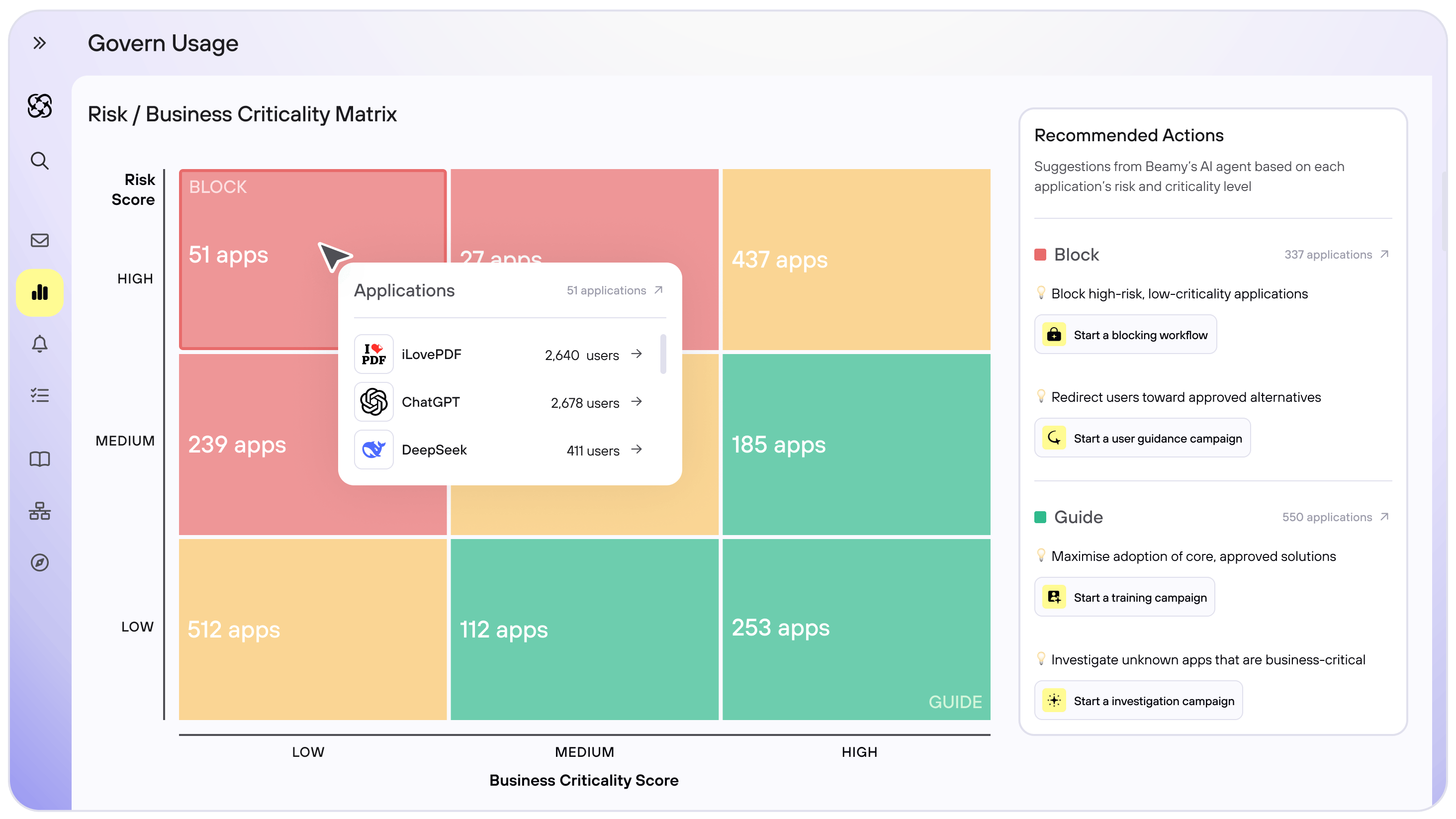
- Use Beamy’s decision matrix to correlate risk level and business criticality
- Enhance blocking capabilities for highly risky, low-value business applications
- Automate blocking of newly detected applications via SSE integrations
Guide employees through application blocking and redirection
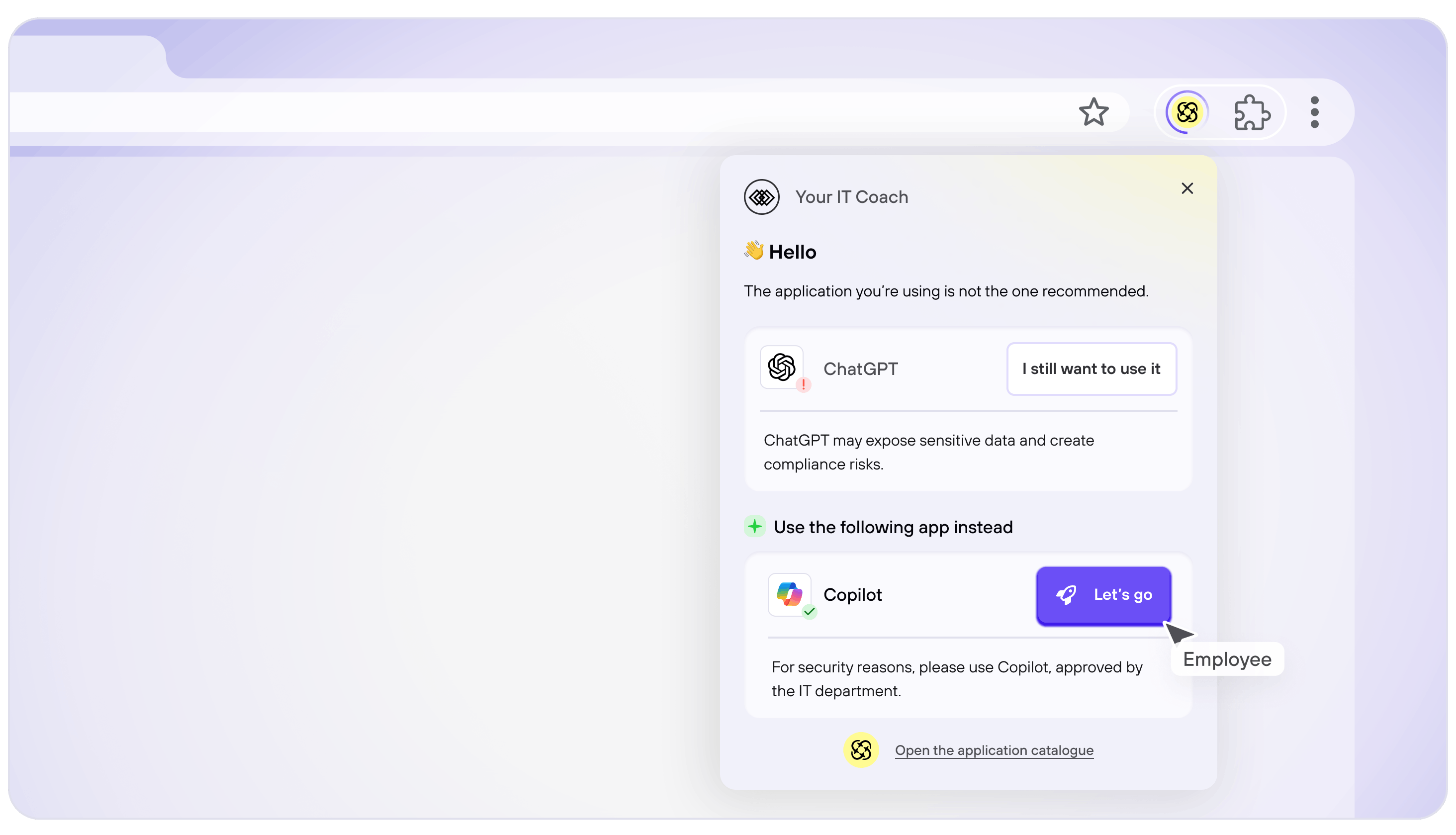
- Notify employees in advance of security policy changes to avoid disruptions
- Redirect them in real time to secure, IT-managed alternatives with a user-centric approach
- Raise security awareness and promote best practices at the right time
